There are many reasons why you might want to spy on someone else’s PC, although not all of them may be ethical, legal, or socially acceptable. While it is possible to engage in this practice, it doesn’t mean that it can or should be done. Whether your motivations are personal, professional, or criminal in nature, there are a series of tools and programs for spying on PCs that will allow you to monitor what a person does with their PC, including their activity, the websites they visit, the passwords they type, or the data they access.
Many parents have concerns about what their children do or don’t do with their computers and consider the method of spying on minors’ internet usage, whether to protect them or to keep them under control. Although there are parental control tools, some parents prefer to spy on their children’s activities without their knowledge. It’s also possible that some bosses want to know which websites their employees visit during working hours or spy on their conversations to learn details about what they think about him or the company. The reasons for resorting to one of these programs to spy on PCs are varied, but as we warn and repeat, having reasons to spy or having authority as a parent or employer does not imply being right or exempt from committing a crime against privacy.
What is considered spying
Let’s break it down… What is considered spying? Viewing the Netflix history of your partner’s profile is not considered spying on a computer or spying on a mobile phone, for example. Nor is opening the computer’s history if it’s shared and both of you use Google Chrome, as it’s assumed that there’s nothing hidden and it’s accessible, something you could have seen for your own use. But, logically, there are limits. Can we read our partner’s WhatsApp messages? Can we install spyware on their computer to find out what they’re doing? Can we install any of these programs on our coworker’s computer? Logically, no. In the case of coworkers or unknown individuals, it seems quite clear that it’s neither legal nor permissible to do so, but the lines blur when it comes to the home, spying at home, or spying on our own partner or family.
This is what the law says.
We can spy on PCs with the help of various programs. However, it is not entirely legal. If we fraudulently access a computer that is not ours and steal or obtain information that its owner does not want us to have, we will be committing a crime against the confidentiality, integrity, and availability of data and computer systems. Some examples of these crimes would be identity theft and the use of spyware and keyloggers, tools used to spy on someone else’s PC in order to obtain information about the websites they visit, the private conversations they have, or even as simple as a click of their mouse. All this data will be recorded and available to the person handling the spy program in question.
Article 197 of the Penal Code
Article 197 of the Penal Code deals with crimes of discovery and disclosure of secrets and refers to programs designed or adapted primarily to commit any of the aforementioned crimes. So we must know that acquiring one of these programs to intercept information, conversations, passwords, or other types of data without the owner’s knowledge can bring us many problems, especially if that information is disseminated, involves a minor, or “when the facts have been committed by the spouse or by a person who is or has been united to him by a similar affective relationship, even without cohabitation.
Article 264 of the Penal Code
And be careful not to delete, appropriate documents, or make any other alteration to information on the spied computer, because in Article 264 of the Penal Code, referring to computer damage offenses, it specifies: “1. Whoever, by any means, without authorization and in a serious manner, erases, damages, deteriorates, alters, deletes, or makes inaccessible someone else’s computer data, computer programs, or electronic documents, when the result produced is serious, shall be punished with imprisonment from six months to three years. 2. A penalty of imprisonment from two to five years and a fine of ten times the amount of the damage caused shall be imposed when any of the following circumstances concur in the described conduct (…) The offense has been committed using any of the means referred to in Article 264 ter.”
Is it the same as parental controls?
Spy programs or applications are not included in parental control programs. There are many tools that allow parents to know what their children are doing on the internet in a completely legal manner and with the sole purpose of safeguarding their safety and privacy. In this case, the programs offer us functions and tools to know what websites they visit, what applications they can or cannot download, and what content they can or cannot see.
Some, like YouTube Kids, allow us to protect young children from adult content, and major streaming services have parental controls such as Netflix, HBO, etc. In these cases, it’s not about spying but about monitoring and caring for what they see, what they do, or who they talk to, due to the risks and problems that young children may encounter on the internet.
In parental control tools for teenagers, such as Google Family Link, the young person in question must give consent to access their location or data remotely to know where they are or what they are doing. But this wouldn’t be considered spy programs since it’s understood that we are responsible for supervising what a child does on the internet. Additionally, the teenager “agrees” to allow their visits or activities to be seen, so we are not doing it without consent.
How to know if we are being spied on
Just as we want to spy on others, with a series of programs that we will leave you below, it is possible that someone may want to spy on us. Knowing if our computer has one of these programs installed is not always easy, but sometimes there are a series of symptoms that can make us raise the alarm. Below, we will show you a list of some of the most common ones that should make you suspect that someone may have installed such software on your computer. It doesn’t always mean that you have spyware, but it may give you some clues that something is wrong. Or at least, unusual.
How to detect it on the computer
If you suspect that your computer has one of these programs installed, we recommend using a program to detect and remove spyware. You can also use Task Manager to identify malicious programs and uninstall them, although these types of programs generally hide very well.
Sluggish Performance:
The computer is running slower than usual. While this may not directly indicate spyware, a slowdown without any apparent reason could be a symptom of malware installed on the computer. There could be various reasons for a slow computer, and it’s not always because you’re being spied on, but it could be one of the causes.
Strange Behavior:
The computer behaves oddly. Programs you didn’t install may appear, windows you didn’t open pop up, desktop icons move around, or chat windows open in messaging apps. Pay attention to sudden program closures or unexpected Windows messages or alerts.
Drained Battery and Increased Data Usage:
The battery drains faster than usual, or there’s an unusual increase in data usage or bandwidth consumption. This could be caused by spyware. While this is more commonly associated with mobile phones, it’s possible you’ll notice rapid drainage on a laptop as well.
Unrecognized Programs:
There are numerous programs available for tracking our activities. They can be added to our computer without our knowledge, and the person who installs them doesn’t even have to be physically connected to the computer.
Remote control programs or virtual network software allow the installer to see all actions. To check for these programs, go to Start and search for running programs. Click on “All programs” and see if any of the programs like VNC, RealVNC, TightVNC, UltraVNC, LogMeIn, GoToMyPC, etc., are installed. If one of these programs is installed, someone could be logging into your computer without your knowledge.
Additionally, if someone installed a new keyboard cable, new software, or updated or repaired the computer, especially in cases of harassment or surveillance, it could be a cause for suspicion. Be cautious of gifts from unfamiliar individuals, as they could contain spyware.
Using a program to remove spyware
If you suspect that your computer has one of these programs installed, we recommend using a program to detect and remove spyware. You can also use the Task Manager to identify malicious programs and uninstall them, although these types of programs often hide well. There are many specialized programs that can conduct a thorough scan of our computer and let us know if anything is improperly copying information. These programs are generally not visible to the naked eye and are hidden, so it’s best to look for specialized software or contact an expert who can detect these types of spyware programs and then report them. If you suspect your computer isn’t functioning as it should or simply because of personal signs that lead you to do so, look for specialized software and scan your system.
The best spy software for pc
Although many of these spy programs are sold explicitly for monitoring children and employees, they have no control over how we use them, and we can use them for any purpose, spying on whoever we want, once we have assumed that this behavior, beyond ethics and morality, may constitute a crime. There are several spyware programs that will help monitor someone else’s PC, both keyboard activity and visited pages, as well as other functions for complete espionage.
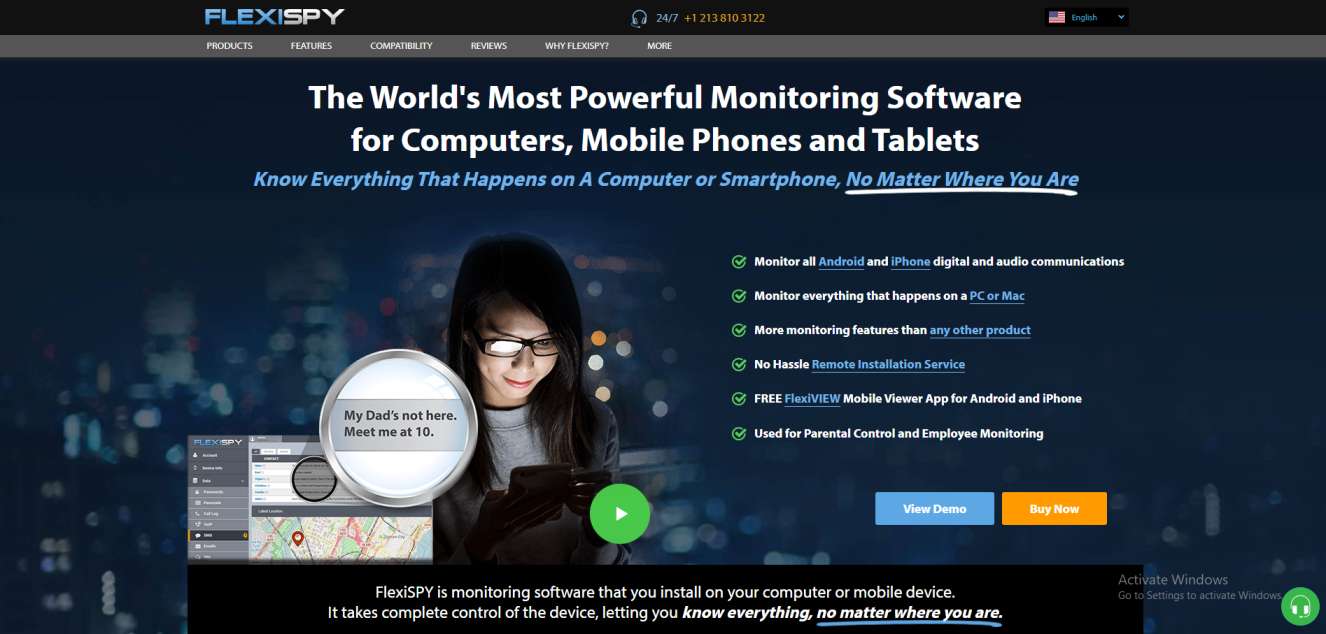
FlexiSPY
This computer monitoring software, as described, has access to multiple data and among its functions are:
Monitor instant messaging: Spy on instant messaging chats such as Facebook or WhatsApp and log all words.
Spy on internet activity: Records history, bookmarks, browsing history including URLs, date and time of visit, and keeps a log of all network activities on the computer, including logins.
Keylogger: The famous keyboard keylogger, which traces all the words that have been typed, whether in conversations, search terms, or private documents.
Tracks sent and received emails: It is able to read all incoming and outgoing emails.
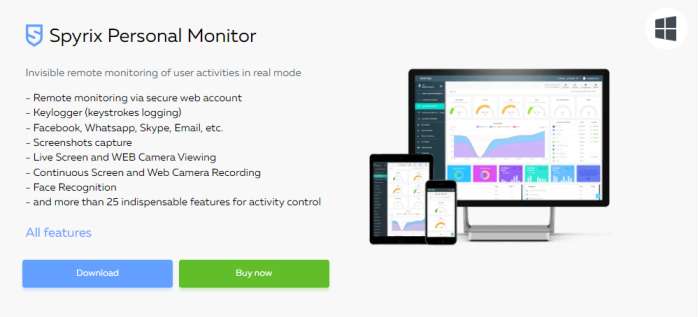
Spyrix Keylogger
This software has different variants for different uses and ensures that it is updated daily to be invisible to antivirus software and can act in stealth mode, without being perceived by the person being spied on. The main functions of its Spyrix Personal Monitor version are:
Record visited websites:Records websites visited by the user. It logs all information entered by the user on sites such as emails, different passwords, chats, and screenshots of websites.
Keyboard activity: Records and monitors keystrokes made by the spied-on computer.
Instant messaging control: Skype, Facebook, Twitter, and other applications will be recorded, and sent messages can be viewed, as well as passwords entered on these social websites.
Live view: Allows you to view the screen of the spied-on computer live and securely remote monitoring.
With PRO license: Takes instant snapshots from the user’s webcam, voice surveillance microphone, and webcam surveillance.
Spyera
This software, defined as the most powerful for Windows and undetectable, allows monitoring the activity of another PC, recording screenshots, and even capturing conversations held through chats such as WhatsApp Web or Facebook. Among its features are the following:
Keylogger
The key to all these spies, which involves seeing everything that is being typed on the spied-on computer. Every keystroke is recorded for review, including instant messaging chats or emails.
Record screenshots
Allows capturing the screen of the spied-on computer to steal shots and know at all times what the person at the controls of the spied-on computer is doing, where they are browsing, or who they are talking to.
Spy on emails
Controls and tracks all emails, both from the inbox and sent items, as well as additional data such as the time the email was received or sent and sender details.
Revealer Keylogger
This is the most popular monitoring software and has two versions, one free and one paid where additional features such as screen capture or remote monitoring are added. Its free version allows protecting the program behind a password so that no one can open it, described as the best option to know what is happening on your computer. Among its features are:
Conversation monitoring
It is capable of recording all keystrokes, so the user will be aware of all conversations taking place in instant messaging or social networks, including passwords for these accounts.
Screen captures
This is a paid service not included in the free version. It constantly creates screenshots that can then be consulted to know when Internet access occurred and which pages were visited.
Remote monitoring
Also included in the paid version, it allows checking what is happening on a computer without having to access the computer, as it sends the recorded files for remote consultation, with the temporal frequency that the user prefers.
Best Free Keylogger
It is also described as a solution for monitoring the activity of children or employees during working hours, although like the rest, it does not have tools to verify that this will indeed be the use given to the Keylogger. Some of its key functions for spying on a computer are:
Total control
It records all keystrokes, as we have seen in other similar programs, allowing us to indirectly read all conversations. It also monitors internet activity, clipboard usage, and the use of local applications. Periodic screenshots can be scheduled at established intervals.
Hidden and undetectable work
It operates invisibly in the background, password-protected. It ensures that only the user who installed the software can view or open it using the password and that antivirus programs are unable to detect its activity.
Remote report sending
It is not necessary to access the spied computer to check its activity. It generates reports that are sent via email or FTP, in addition to the option of viewing them on a computer on the same LAN as the one where the software is installed.
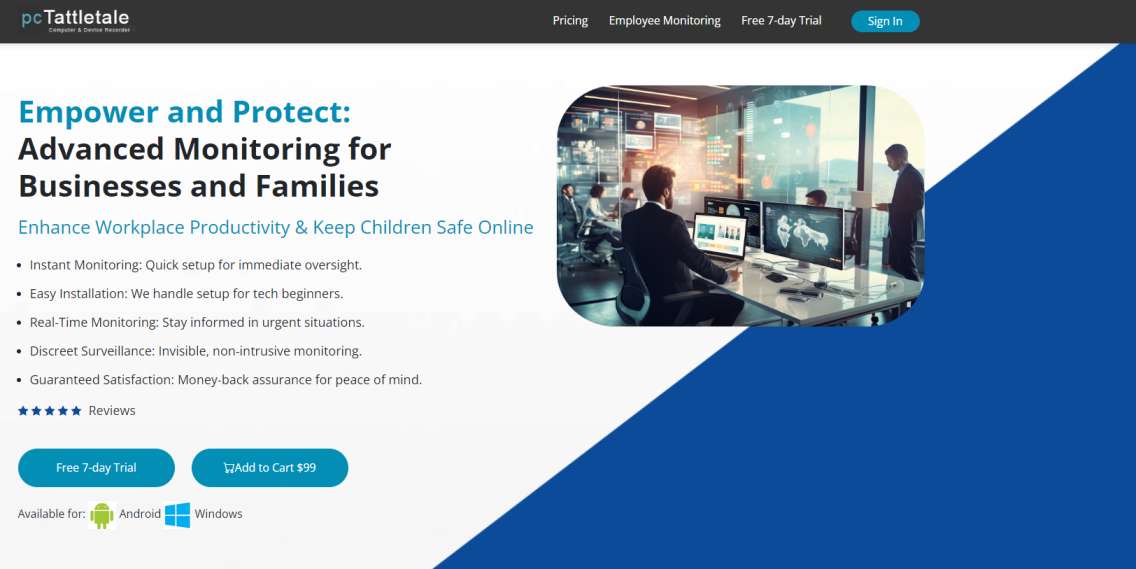
pcTattletale
This software offers the ability to monitor a remote computer by recording the device’s screen. However, the program is not yet available on Mac computers, but it is present on the following Windows versions: XP, Vista, 7,
8, and 10. Additionally, it is specifically designed for monitoring employees, as no clues or notifications are provided that their computer is being observed.
The time difference between real activity and live recording will be about 10 to 15 seconds, which is quite insignificant. Live recording may not show precise results while the user is playing any video on their laptop. Therefore, it may get stuck on a particular screen while the user continuously plays a video (such as watching a movie on Netflix).
It has few features, although the main one is that it records the screen of the target laptop. Once the spyware software is installed on the computer, this program remotely records the screen without giving any clues to the other person. The recorded activity can be viewed remotely at any time using the playback button. Through a playback button, we can remotely view both previously recorded and live content. In this regard, pcTattletale incorporates a kind of calendar that allows us to select the desired date to check the screen recordings for that day. It is also possible to download the activities for each day.
With pcTattletale, we can also easily check the total number of clicks made on a device from one hour to another. Based on this data, we can find out how much time our child spends on the computer, for example. If we enter the Activity section, it will reveal the amount of computer usage, and in the App Usage section, the name of the most used application will be displayed.
MoniVisor
Another very interesting alternative in this category is MoniVisor, although, in this case, it also serves to spy on someone’s mobile phone, not just their computer. If we want to download this software on our smartphone, we must search for it by the name KidsGuard Pro, which is what it is called on these devices.
Returning to the computer, the compatibility of this program is limited as it is not available on Mac and is only compatible with Windows 7, 8, and 10, which reinforces the image of security and privacy that Apple devices project. For now, it is unknown if it will reach more operating systems via updates
Total Spy
It is a very intuitive and easy-to-use program, so you won’t have any problems working with it. In addition, one of its great advantages is that you can camouflage it so that no one else (except you) can find it on the installed device. Through this spying software, you can know all the activities carried out on a computer. In fact, it records and stores all written messages sent (emails, conversations on social networks or Skype, among others), the programs that run on the system as well as the URLs of the visited websites (that is, the browsing history).
Similarly, with Total Spy, you can explore the clipboard and take screenshots of exactly what other users have done. For example, the program automatically takes screenshots of other users’ social networks. You can also set a timer on the “screenshot” option and decide how often you want the images to be taken. However, we must emphasize once again that accessing other people’s social networks (without prior consent) is completely illegal.
What to look for when choosing one
If you have decided to install spy software, it is very important that you consider the following tips to make the right decision and not be deceived.
Security
One of the main keys to choosing the spy program you are going to use is your own security. Therefore, make sure that the program is trustworthy and will not cause problems on your computer or mobile device.
There are many cybercriminals who take advantage of the fact that people want or need to spy on a PC, which can have a rebound effect. Instead of spying, they will be spying on you or something worse! Do not trust bargains or applications that promise too much.
Effectiveness
The key to your decision should be primarily motivated by the effectiveness of the program. This means that it is able to fulfill the functions it offers effectively and quickly. To know if this is the case, you can consult opinions from other people or look at the features it has. It will also depend on the functions you want to use. If it is for spying without someone knowing, we may be limited. On the other hand, if we want to use a program as a remote control, the effectiveness will be greater.
Versatility
A highly advisable aspect is its versatility, the capacity of the chosen software to fulfill its function and provide you with more features. There are programs that not only serve to spy on your PC but also offer many other functions. They can track a mobile phone, monitor certain movements, and much more. There are also some that provide access to the microphone and webcam.
Functioning
Understand how the spy program works to discover how it is giving you results and trust them more. It is important to pay attention to the features and functions, to the specific characteristics of each of the programs you are interested in.
If you have any doubts, consult a manual or look at reviews from other people before deciding on the selected program.
Ease of use
Considering that you are looking for a specific program with certain functions, it is necessary that it is easy to use. This way, you can do whatever you want with it in much less time, which is advisable when you are spying on someone and time is against you.
If you familiarize yourself with the platform from the first moment and know how to use it effectively, it will be much more attractive to you. But above all, you can make the most of your time.
Price
The cheaper the program, the better, and even more attractive if it’s free! However, in this type of products, we recommend that you pay close attention to what you are going to acquire. Many free apps or programs are of dubious credibility or will not give you the results you were looking for.
In this case, the price will matter; the cheaper, the better, but look for something that fulfills its promises and adapts to your specific needs.
What is the best case?
Throughout this article, we have shown you the best programs for remotely spying on a computer. However, which of these software stands out above the rest? Although all or the vast majority share advantages, we must decide which one adapts best to our situation if we want to use one. Something that we totally discourage from here, as we have explained in the initial part of the text.
For example, MoniVisor can be very useful if we want to take that spying beyond someone’s computer and delve into their mobile phone, a feature that is not present in virtually any other similar programs and sets it apart from the rest.
If we want to limit our activity to a computer, perhaps the most recommended program is Flexipyrix Keylogger due to its wide range of options, ranging from real-time monitoring of activities being carried out remotely to control of instant messaging and keyboard, two points to be taken into account in these cases.